The sophisticated supply chain attack that is dubbed “Operation ShadowHammer” has compromised one of ASUS’ servers which is used to provide updates via the ASUS Live Update utility tool.
Researchers at Kaspersky Labs had uncovered the attack in January 2019 however, investigations are still in progress and full results and technical papers will be published during SAS 2019 conference in Singapore.
ASUS Live Update is an utility that is pre-installed on most ASUS computers and is used to automatically update certain components such as BIOS, UEFI, drivers, and applications. According to Gartner, ASUS is the world’s 5th-largest PC vendor by 2017 unit sales. This makes it an enticing target is given the size of their userbase.
Kaspersky has reported that over 57,000 Kaspersky users have downloaded and installed the backdoored version of ASUS Live Update at some point in time and the malware was estimated to have affected over half a million ASUS users using other antivirus software.
The hackers gained access to the ASUS Server and were able to fraudulently sign the trojanized malware files using an authentic ASUS digital certificate.
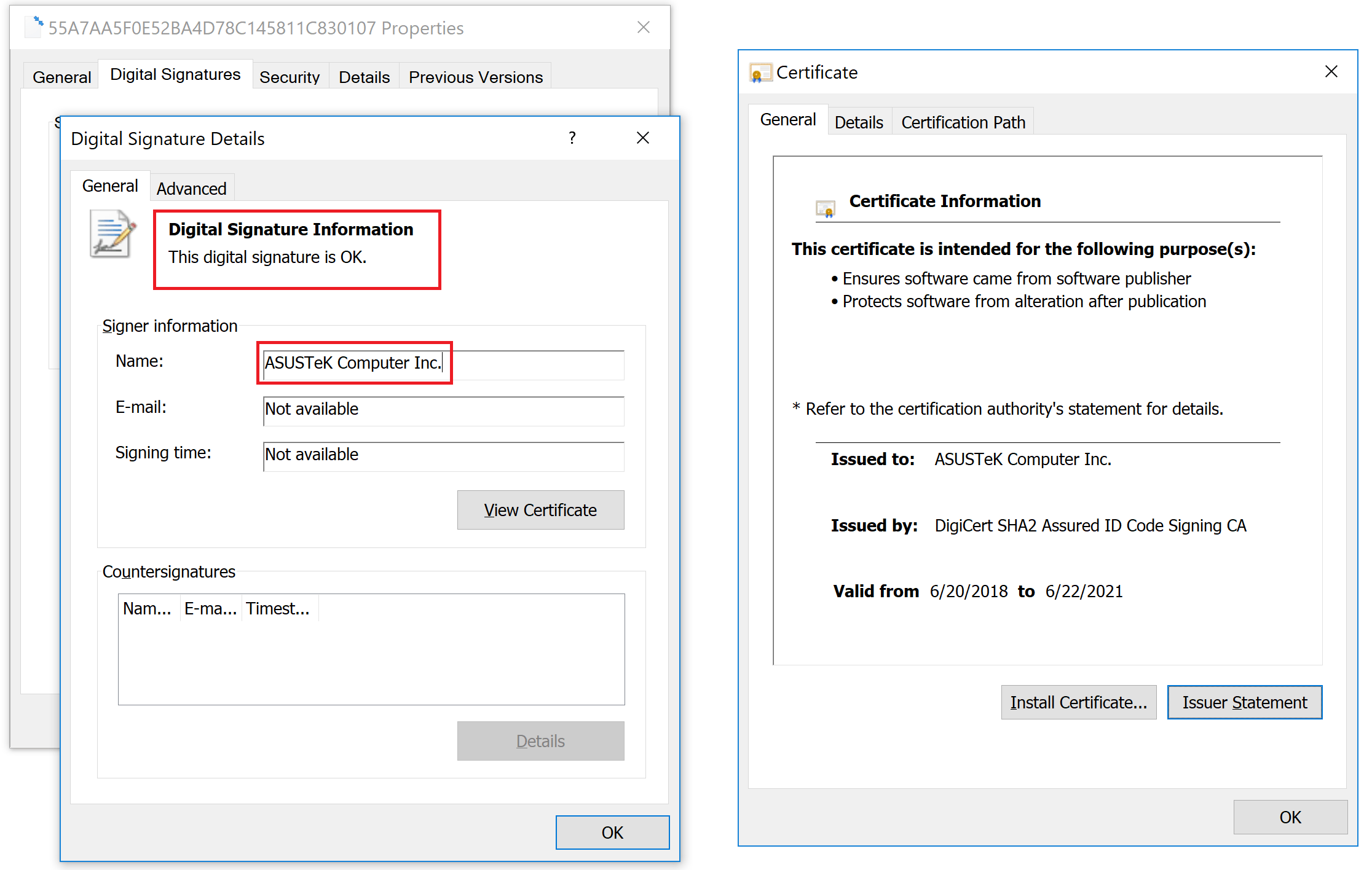
Digital signature on a trojanized ASUS Live Update setup installer
The malware targeted an unknown pool of users, identified by their network adapters’ MAC addresses but some evidence collected by Kaspersky correlated the attack to the ShadowPad attack in 2017. The perpetrator behind ShadowPad has been publicly identified by Microsoft in court documents as BARIUM. BARIUM is an APT actor known to be using the Winnti backdoor.
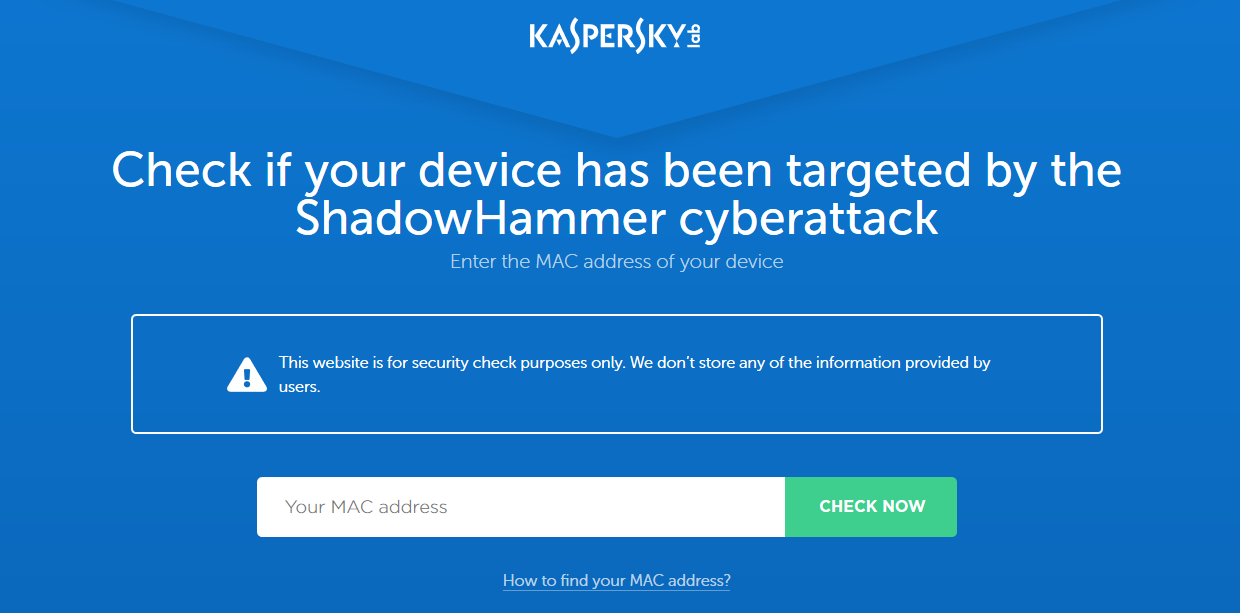
As a result of this attack, Kaspersky Labs has created a tool that can be run to determine if your computer has been one of the surgically selected targets of this attack. To check this, it compares MAC addresses of all adapters to a list of predefined values hard-coded in the malware and alerts if a match was found.
Download an archive with the tool (.exe)
Also, you may check MAC addresses online. If you discover that you have been targeted by this operation, please e-mail us at: info@leslieleefook.com.
